Thinking about VOIP security in general
Over the last 8 weeks, we’ve talked about specific challenges in VoIP and communication security – we’ve talked about toll fraud, TDoS, Remote worker security, and so on – going a little bit into each of them. Let’s briefly change track – instead of talking about specific threats and scams, I’ll talk about what I have seen about the state of VoIP security and how it maps onto the larger domain of IT security in general. Here are the things I’ve learned:
Trust is critical for business.
If you believe that trust and reliability go hand-in-hand and that communication is critical for your business, communication security is paramount. Communication systems are subject to the same level of scrutiny from threat actors as data networks. However, data networks are given far more attention than voice networks. This leaves the door open to serious business disruption and loss.
Voice networks, like websites and databases, are applications on the data network, so there are substantial similarities in securing them.
Despite this, we can see that security principles that are regarded as basic in the data world are ignored in the voice and video world. Example: 28% of the SBCs have one or more administration interfaces directly exposed to the Internet (including ancient, outmoded, terrible-for-security protocols like Telnet and FTP)! Almost half (49%) of the SBCs have unsecured interfaces enabled (HTTP, SIP)!
Voice networks, even over IP, have significant differences from data networks, enough to need specialized solutions for security.
Just as data applications (ranging from WordPress to SAP) need specialized security scans and tests because of the unique interfaces they expose to the Internet, so do voice applications. Vulnerability Analysis (VA) systems and firewalls simply do not have the intelligence needed to guard voice applications against attacks. For example, if a SIP call is coming from a known ‘bad’ phone number, normal data security systems would not know how to protect against that. SBCs offer some of these capabilities, but they need access to a constantly updated ‘bad list.’ At this moment, there are over 20 million numbers from around the world that are known to be linked to fraud and threat actors. Even the best configured SBCs do not leverage this knowledge.
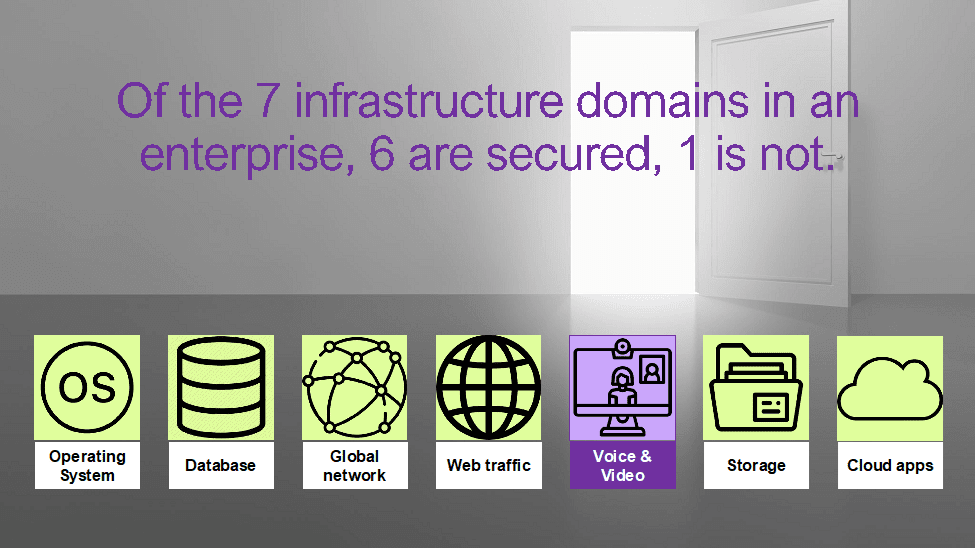
Communication and Collaboration teams need greater investment in security – to get on par with corporate InfoSec practices.
Voice networks are a new attack surface for modern threat actors! Attacks on collaboration systems are up 600% year-over-year! The data we’ve collected over the last few years in our VoIP security report proves that communication and collaboration teams need more training to understand what matters in security. For example, many SBCs supported TLS 1.1 or below – a protocol that can be hacked by spending less than USD 100 today. No team that knows that TLS 1.1 is so easy to break would support such a protocol. By extrapolating the data we’ve collected in the field, it is possible to assume that almost 1 out of 5 SBCs support outdated, deprecated, and unsecured protocols.
You need tools that specialize in communication security.
The unwritten assumption seems to be that data tools are sufficient to address the security requirements of voice and video. To those who make this assumption, we ask: how does a tool that cannot recognize SIP hope to secure it? SIP is a full communication protocol, and if HTTP servers need web application firewalls to protect them, SIP requires SBCs to do the same. But that’s just the beginning – SBCs need additional solution support, which is often unavailable. For example, SBCs can deny access to phone numbers, but getting access to a worldwide database of fraudulent phone numbers is surprisingly difficult. SBCs, like firewalls, are powerful tools, but they only work well when properly configured and monitored.
Organizations need to start inserting security as a key consideration into planning and designing their voice and video networks.
Our research found significant security design issues in the SBCs we scanned. As mentioned before, almost 49% of the SBCs support unencrypted, unsecured SIP and HTTP. 4% of the SBCs still support Telnet, which is less of a protocol and more of a zombie – an ancient, dead being that still stumbles around and bites hardworking operations teams.
Organizations need to build proper security practices around their VoIP apps.
Lack of security processes is visible in many ways: almost 1 in 4 of the SBCs scanned had expired certificates – literally, every packet from such an SBC needs to be untrusted. The only possible reason why SBCs are in such poor shape is that operations teams are unaware of these shortcomings. This goes back to two of the big gaps in communication security: lack of knowledge and lack of tools that give critical information to the teams.
VoIP teams need better support through tools to secure their systems, and the industry is beginning to pay attention.
We know certain OEMs are now releasing additional tools that take voice and video perimeter security to the next level. This is a moment for me to pitch our product — at Assertion, we built Assertion® SecureVoice™, a vendor-agnostic tool that helps companies prevent and detect threats to their communication systems.
Have more questions? Send me an email at securityeducation@assertion.cloud
About Assertion:
Assertion® is a leading communication security solutions provider that empowers companies to Collaborate Confidently. Our ultimate goal is to secure every conversation through our advanced AI-enabled collaboration security solutions. We secure your communication networks, protecting you from data theft, revenue loss and reputational damage by
- Identifying and blocking Robocalls and Scam calls
- Stopping Telephony Denial of Service attacks and Toll Fraud attempts in real-time
- Detecting and eliminating threats to Remote workers
We also provide holistic infrastructure security for over 38 collaboration products, including full-stack collaboration security solutions for the UC and CC stack.
