In 2021, as per the FBI, more than one thousand Americans were victims of TDoS (Telephony Denial of Service). The number of organizations that suffered this kind of attack is unknown. But we have some signs:
- The 2016-2017 TDoS attack against Phoenix area ECCs/PSAPs (the 811, 911, and other systems): The attacker had created malware that was distributed through app stores – unsuspecting users had become part of a telephony botnet. When triggered, their devices repeatedly called 911 and the resulting spike disrupted call capabilities at local ECCs/PSAPs.
- In 2019, TelePacific Systems’ telephony systems crashed because of a Distributed TDoS attack. The attackers simply sent a ton of invalid VoIP registration requests. Telepacific Systems, used to handling around 34 million calls per day, suddenly received 69 million calls in a day. Customers simply could not place calls anymore. The result: the company ended up paying hundreds of thousands of dollars in customer credits.
- The Department of Homeland Security published a fact sheet on the challenges of DDOS.
- CISA published a note advising organizations on how to prepare for TDoS attacks on their infrastructure.
- And then followed up with another note on lessons learned from a live attack.
- The FBI published a note on the challenges of TDoS.
Big picture: a significant number of people consider TDoS to be a real problem.
A Telephony denial of service (TDoS) attack is where attackers make a very high volume of calls to the target systems, and keep those calls active for as long as possible, preventing regular, legitimate calls from coming in. As with all attacks, TDoS can be done in any number of ways, from the remarkably simple to the extremely complex. Some examples:
- Someone convinces many people to call a number – that’s it! This is a manual TDoS attack.
- Someone installs malware on people’s communication devices (mobiles, softphones, and so on), converting the phones into a zombie army that, on command, calls a specific number or range of numbers. This is a distributed TDoS attack.
- Someone breaks into a PBX and uses this as a weapon to target-call a specific number.
If a VoIP system is being attacked, the attackers usually spoof numbers to avoid getting caught. The common element in all of these is that they target a single institution or organization and bring its communication system to its knees.
Let’s look at a simple example of how such an attack works.
The Groundwork of TDoS Attacks
Assume Joe Mischief wants to have a few laughs at the expense of the world.
- He uses IoT search engines like ZoomEye, Shodan, and Censys to look for PBXs or SBCs.
- He then probes these SBCs and PBXes, looking for weaknesses. The usual technique is to look for vulnerabilities mentioned in the Common Vulnerabilities and Exposures (CVE) database and see if the systems are patched. If they are not, he has an easy way in. Remember, most hackers are lazy – they are interested in easy wins. It’s only a small number of supremely motivated hackers who are willing to get into the nitty-gritty of systems to discover and exploit new vulnerabilities. And these are usually employed by state actors or rival companies.
- Joe Mischief breaks into one or more PBXes and gets them under his control – they are now his zombies.
- Joe also identifies the target organization – researches and finds out their phone numbers and if possible, more details such as its traffic capacity.
The TDoS Attack
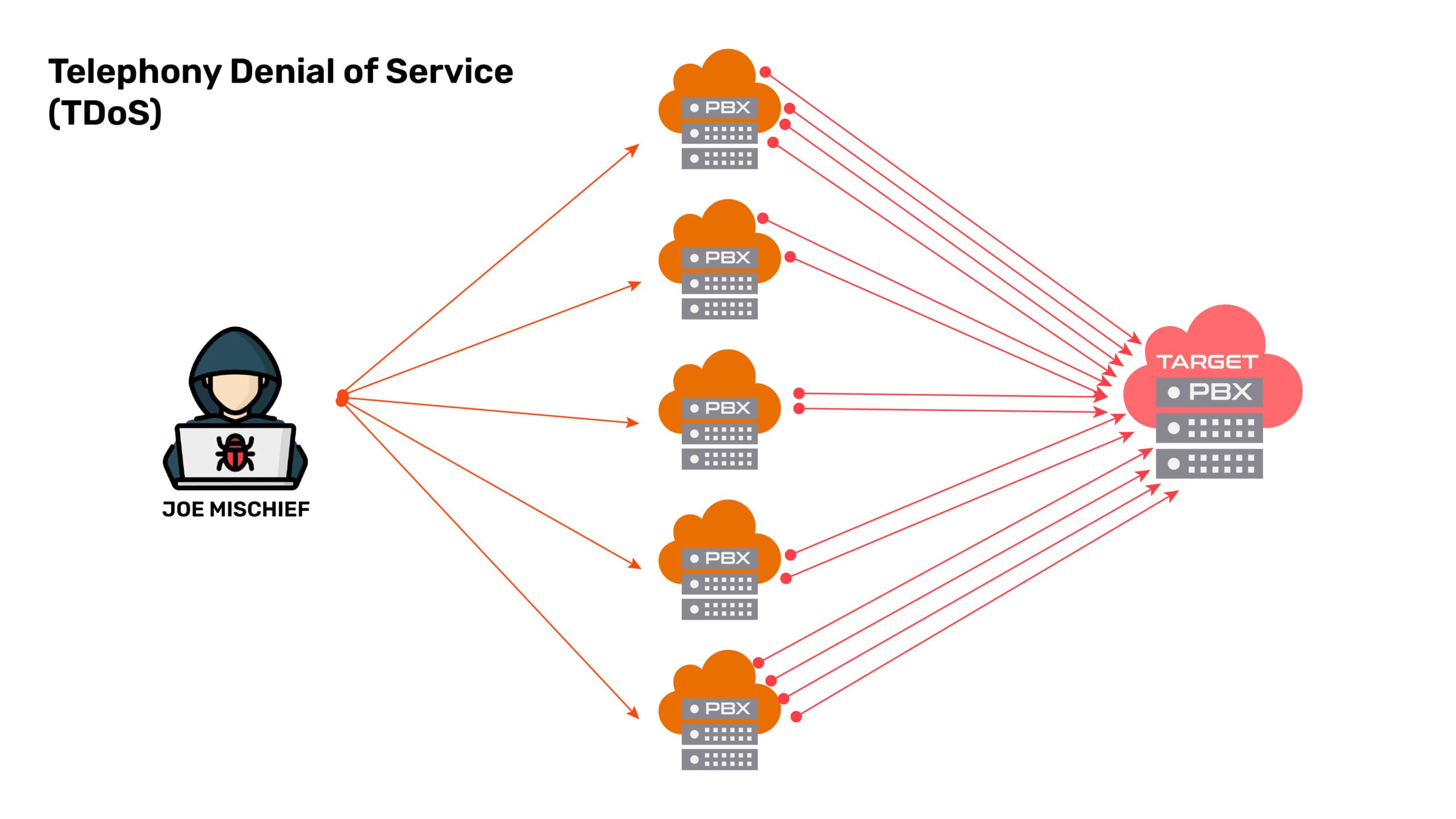
- Joe launches a series of calls from one of his zombie PBXs to the target system. The target experiences a sudden spike in calls. But the received calls are empty.
- If the administrators identify the numbers the calls are coming from and block them, Joe simply switches over to the other zombie PBXes and activates them to make calls.
- Agents/Employees of the company are unable to call out or receive incoming calls.
- If the system is poorly configured, even internal calls become impossible to make.
Note that in the example I’ve given, there are really two victims, the business that owns the zombie PBX and the target business. Both suffer significant pain and liability exposure.
The Point of TDoS Attacks
Why do attackers go in for TDoS attacks? What do they get out of it?
The biggest motivations seem to be:
- Ransom: The message is simple – ‘lovely business you’ve got here. Shame if something were to go wrong with it.’
- Fraud: In a retail variant of TDoS, someone keeps calling targeted individual numbers, keeping them busy. The victims cannot receive calls from their financial institutions while the attackers fraudulently withdraw money from their bank accounts. (Source: FBI)
- Political/Ideological: The equivalent of causing a riot.
- State actors: State actors test the defenses of critical infrastructure (the 911 systems, the hospitals, and so on) and bring them down, as part of an ongoing low-level, undeclared cyberwar.
Preventing TDoS Attacks
The usual method of preventing a TDoS attack from overwhelming your network is to respond quickly and block number ranges (or IP addresses) from where the flood of calls is coming in.
Another technique is to configure limits on your SBC – if the percentage of connection requests or calls exceeds a limit, the SBC can block new incoming calls.
Smarter approaches include scoring all calls coming into the network and rejecting those that exceed a certain risk score. This would involve using tools that can examine multiple aspects of a call in real-time: protocol-level examination to distinguish between legitimate and fraudulent calls, database lookup of known problem IP ranges or addresses, and so on.
Talk with your OEM or your SI partner and see if they can provide solutions that provide this capability. If you have budget constraints, they can still advise you on configuring your communication infrastructure to prevent or reduce the occurrence of TDoS attacks.
Have more questions? Send me an email at securityeducation@assertion.cloud
