From one extreme to another. When I talked about toll fraud last week, I mentioned that huge chunks of the toll fraud scam are automated. Today, I talk about the other extreme – enterprise vishing – a scam that’s so custom, manual, and research-driven, I want to give those Visher’s Amazon gift vouchers as awards for self-motivation! You’ll see why.
Before we get into the what and the how of vishing (‘scam calls’, for the regular folk), some context: If toll fraud is like a mechanized trawler using huge nets to catch whole swarms of fish, vishing is like fishing – using guile and cunning to hook individual ‘fish’. In enterprise vishing, the ‘Visherman’ goes one step further, using the hooked fish as bait to see if bigger fish can be caught. No one knows how big enterprise vishing is, but the hints are hard to miss…
- Chinese hackers using phishing and vishing techniques to scam USD 18 million+ from the Indian arm of an Italian MNC (source – https://www.reuters.com/article/us-mairetecnimont-india-fraud-idUSKCN1P40KE)
- Russian pranksters used vishing techniques to fool the Defense secretary of the UK, Ben Wallace, into a conversation with the ‘Ukrainian Prime Minister’, where he shared some sensitive information about weapons transfers. (source – https://www.theguardian.com/world/2022/mar/21/video-released-showing-russian-hoax-call-with-uk-defence-secretary
Vishing is a social engineering attack – calling someone up and convincing them to do things (approve transactions, for example) or reveal information (PII, PHI) that they normally wouldn’t. Vishing is very effective – a study showed that as many as 37% of vishing attacks succeed! It becomes even more effective when tag-teamed with phishing (sending emails to someone and getting them to click on links in the email) – the same study showed that almost 75% of these tag-teamed attacks were successful!
Nearly all vishing attacks are financially motivated – getting access to information that is valuable/useful/financially remunerative. The BBC gives a good example of a retail-level scam call: Emma Watson, a British businesswoman, got a call from her bank’s fraud team. They said they had spotted and paused some odd transactions originating from her account. When she confirmed that she had not initiated them, they explained that her account was probably hacked and that she needed to move her money to another account. They then proceeded to guide her through the steps needed to transfer the money into an alternate account created for her. What a nice bank, she probably thought, until she later realized that this itself was a scam call. Outcome: more than 100,000 GBP lost!
How does vishing work in the enterprise?
The model for vishing in the enterprise is like retail-level vishing, but with several enterprise-level characteristics. The key differences shown by the scam artists are more research, more groundwork, and higher stakes. Here’s an example, discussed by the FBI – https://www.documentcloud.org/documents/7041919-Cyber-Criminals-Take-Advantage-of-Increased.html
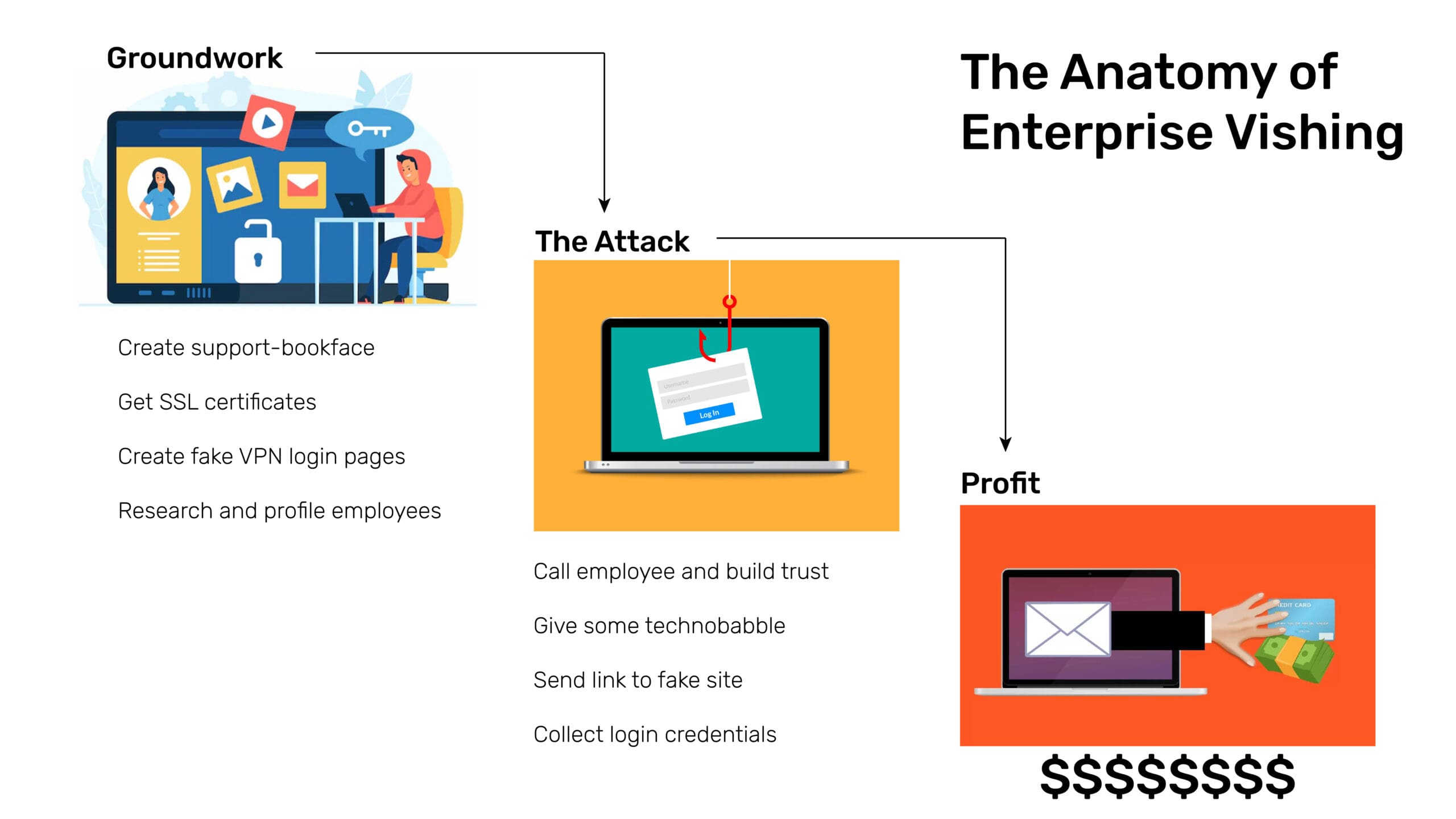
The Groundwork
Assume Joe Fraudster, as part of his diversification from regular petty fraud like cheque fraud, has decided to go upmarket and get into scam calls, or what his techy-boys call – vishing!
Joe decides to target BookFace, a major call center.
- He creates sites such as support-bookface.com, employee-bookface.com, bookface-support.com, and so on and then gets SSL certificates for them.
- Joe then gets hold of the VPN login pages of BookFace and duplicates them on these sites.
- In the meantime, Joe’s minions are all over social media (LinkedIn, Facebook, Instagram, Twitter…), looking for employees of BookFace. They build dossiers of information about these employees, replete with details such as their complete name, address, designation, phone numbers, duration at the company, and so on.
Now it’s time to unleash the attack!
The Attack
Joe’s minions are expert talkers – they know how to make people comfortable, using the right mix of formal and informal conversation.
- The scam artists make normal VoIP calls or use spoofed phone numbers that resemble the target company’s phone ranges to employees’ personal cellphones.
- Using the profiled information collected through LinkedIn etc., they win the trust of the victims.
- By pretending to be co-workers trying to solve technical issues, they convince employees to click on links in the emails sent from the fake sites that Joe has set up. When the employees enter their account details on the VPN login – the scam artists use that information to log into the company’s account in real-time. Even methods like 2-factor authentication fail here: the victim enters the 2FA or OTP passcode into the website, and the scamsters simply reuse it to gain access.
- Using the access they have, the scamsters now begin to gather more information, and in some cases, use the access to fraudulently transfer money.
- Finally, they use information gathered to scam more employees and gather even more substantial information, including customer information, which they can then use to scam the company’s customers.
The research, groundwork, and social engineering expertise required is substantial, but the payoff for Joe and his gang of scamsters is significant too. The BBC tells us that social engineering (and scam calls/vishing belongs to this category) is now a unicorn – a billion-dollar per year business but the CFCA tells us that phishing itself is a 1.62 billion business. Now you can see why they are so motivated!
Plus, it lays the groundwork for all kinds of secondary crimes including malware, ransomware, financial theft, fraud, and so on… the gift that keeps on giving.
Preventing Scam Calls
Fighting scam calls is a complex problem – otherwise, I wouldn’t write an entire article about it.
The most common advice is to train employees, but usually, a combination of phishing and scam calls with spoofed phone numbers catches even many trained people unaware. You will find tons of advice elsewhere on the Internet, so, let’s spend a moment thinking about the challenge and its resolution purely from a telephony perspective. If you work in an external-facing function of any large company (sales, marketing, finance, collections, procurement, and so on), you will receive phone calls from unknown numbers, and these are unavoidable. Some of them may be scam calls – and it would be good if you had a system that
- checked these numbers against some global or national database
- saw if any were potential (or identified) scam numbers or calls that indicated spoofing of some kind
- blocked the known scam numbers
- flagged the others as per the risk to you, so you could act with appropriate care
In the retail world, tools like Truecaller and Robokiller provide the solution. Enterprises require more robust answers – a solution needs to dive into protocol-level details of incoming calls to see signs of spoofing.
Talk with your OEM or your SI partner and see if they can provide solutions that provide this capability. If you have budget constraints, they can still advise you on configuring your communication infrastructure to prevent or reduce the occurrence of vishing.
In the next article, we shall look at the problem of TDoS attacks and some techniques to prevent them or fight them.
Have more questions? Send me an email at securityeducation@assertion.cloud
