It’s not a VoIP attack, it’s a whole new category! Read more about Remote Worker Security and Stop SBC Hacks.
Personally, I now have 95% of my meetings over the phone or video. I assume it’s the same for every one of you.
- Gartner predicts that, by 2024, in-person meetings will account for just 25% of enterprise meetings, making VVoIP a preferred channel of communication.
- McKinsey survey states, that employees ranked collaboration and VVoIP systems that enable them to dial into remote meetings in the top five policies for the post-pandemic world.
In our context, remote workers are folks who use voice and video communication devices from outside the office. When COVID pushed everyone to work from home, companies scrambled to enable all kinds of infrastructure for remote use. This included a remote worker setup to facilitate voice and video communication for remote workers.
I’ll back up a moment and review a diagram – just so we are all on the same page about terminology.
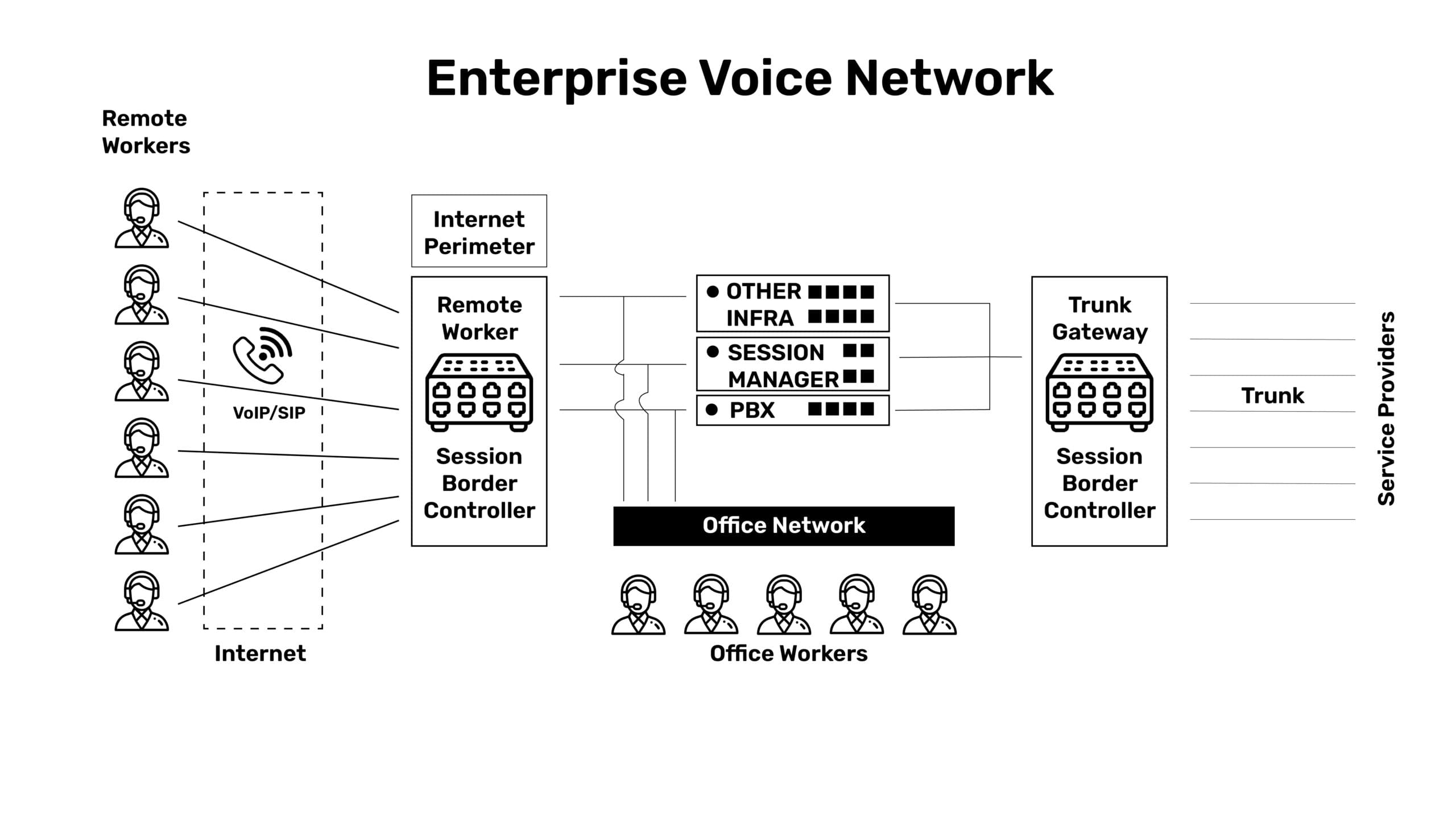
Session Border Controllers (SBCs), deployed at the edge of enterprises, control and regulate all forms of real-time communications including VoIP, video, and collaboration sessions. The diagram above describes a classical remote worker setup for communication infrastructure.
The normal telephony infrastructure is sandwiched between two SBCs:
- On one side, remote worker clients get connected to remote worker SBCs, which act as firewalls and attempt to block bad actors from coming in over the internet.
- On the other, the trunk is connected to another set of SBCs, which block bad actors from coming in from the trunk side.
A little history:
Over the last two decades, companies all over the world have been switching to VoIP (usually SIP) on the trunk side. But because this was a steady and planned move executed over many years, SBC deployments on the trunk side are mature, and therefore, relatively far more secure than the remote side.
Here’s why: Many companies, in the urgency of enabling remote working voice and video, set up remote worker SBCs without paying attention to their security and configuration. Several others simply assumed that dumping a firewall in front of the PBX before enabling remote work was sufficient.
Both are huge security risks. We will discuss why further below.
Last year, Assertion released The State of SBC Security Report, the first-ever study on how secure the voice and video perimeter of most companies is. We found all kinds of interesting (and concerning) data:
- An average SBC gets probed within 5 minutes of going online.
- Over 50% of internet-facing SBCs were at high risk – due to misconfigurations.
- Adherence to basic security practices was worryingly low. For instance, security best practices require that certificates older than 13 months be renewed. But 86% of the SBC certificates we examined exceeded that limit. Of those, 70% were older than 24 months.
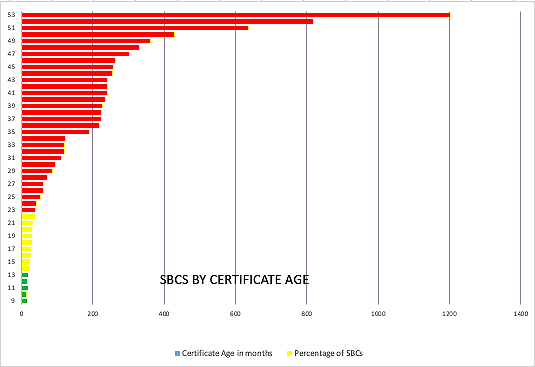
And the thing is, we only reviewed Internet-exposed SBCs. It’s a pretty good bet that most of them are for remote workers. You see, for management and security reasons, most companies keep their remote worker and trunk-side SBCs separate.
The big lesson:
There’s a pretty good chance that remote worker voice and video systems are insecure and exposed to the internet. This means a remarkable number are being attacked and breached!
Now, why is remote worker security such a mess?
- Vulnerability assessment falls short
Standard platform-based vulnerability assessment tools including patch management tools, only look at known platform vulnerabilities such as OS vulnerabilities, databases, webservers, etc. — the SBC, a VoIP system’s only internet-exposed application, is left unchecked.
- Current security-by-design standards fail for SIP
Firewalls, normally installed in front of SBCs, do little for SIP security. They merely pass them through to the SBC, making its configuration and security a high priority. Current models do not investigate the SIP traffic on a call-by-call basis to detect attack any abnormal activity. - Static security reviews offer no real value
Security hardening, typically carried out once a year, operates in isolation without considering what’s happening to the SBC this minute. This means that it fails to review the SBC’s configurations on an ongoing basis and reconfigure them dynamically based on the traffic passing through the SBC. - Zero to low awareness of the types of attacks on SBCs
SBCs are complicated devices and attacks on them pose unique safety challenges. VoIP teams have no way to track and stay updated on the unique security challenges that SBCs face.
These make the security of SBCs a blind spot with:
- No attack visibility till they escalate into breaches.
- No reliable threat intelligence for attack prevention.
- No centralized visibility into multi-vendor or geo-distributed SBCs.
- No integration into standard SOC practices.
In summary, remote worker security is a niche that needs to be studied in more detail – threat actors are already beginning to sharpen their attacks on this attack surface – and it’s up to us to figure out how to protect our networks here. My next article shall discuss some of the key attack vectors for remote workers, and how to avoid being a victim.
Have more questions? Send me an email at securityeducation@assertion.cloud
