In this article, instead of looking at a specific use case and trying to figure out how to prevent remote worker attacks, we will discuss how to prevent a vast majority of such attacks – VoIP security hygiene.
When attackers hit VoIP remote worker systems, they usually:
- Look for data they can steal, such as customer information, company details, address books and so on.
- Attempt toll fraud by calling high-cost destinations and premium rate numbers.
- Try to covertly listen in to conversations, so they can use it for other motives (ransom, blackmail, data theft).
- Attack laterally into recording systems, voice mail, and so on, expanding the scope of the breach.
And if your company is the victim, here is an overview of some of the potential impacts, starting with the least obvious:
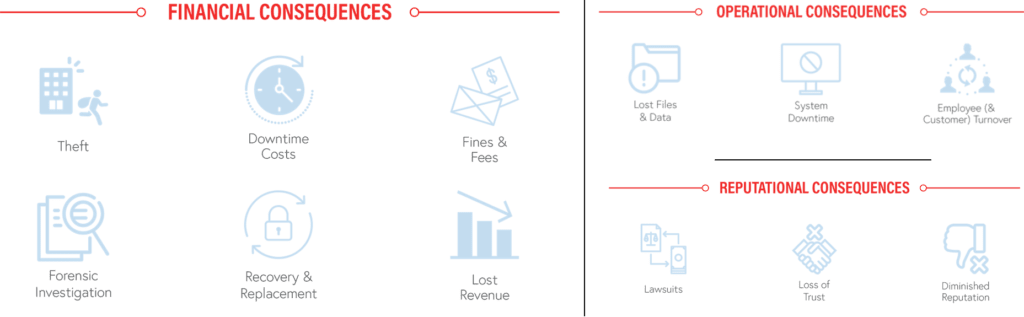
- Fines and regulatory hassles – Since the attackers are an uncontrolled element in your network, it is entirely possible that they may end up causing regulatory violations. For example, the attackers may call OFAC-listed countries such as Iran, Syria, or North Korea, which may invite the attention of regulatory agencies. The agencies may believe you when you tell them it was the action of a threat actor, but do you really want to deal with the hassle?
- Downtime and attention costs – Imagine you coming home one day and realizing that someone had walked into your house in your absence and taken food from the refrigerator. Nothing else was stolen. Are you comfortable with that? I know what you would do – immediately start trying to figure out how the intruder got in, how many times that fellow had gotten in earlier, what else has been touched/taken, and how to ensure that this will never happen again. This takes time, effort, and attention. Now imagine you found out that someone broke into your communication network and made only a few phone calls to premium rate numbers. Are you comfortable with that? You’d have to get a forensic investigation done, look at how the intruder got in, and so on…
- Loss of face: Your peers in the community would see you as incompetent and unable to get your act together. Not fun.
- Impact on brand value: Data loss is a sticky situation to get out of. Even if you don’t have their data, people still see it as a sign that you cannot be fully trusted. Again, not fun. Even employees don’t want to be associated with a brand they don’t trust or respect.
- Revenue loss to resource misutilization: Attackers using up resources, which can be especially difficult if you are dealing with high-demand setups.
- Added costs: Through (i) the cost of a forensic investigation, (ii) scams like toll fraud
So, there is a serious upside for attackers and often, the downside is quite low. Vice-versa for you.
How to prevent VoIP remote worker attacks from succeeding
In my earlier article, I have briefly mentioned defense in depth – the idea of having multiple obstacles in an attacker’s path – to make sure that the attacker is slowed down/demotivated in his attempts to break in.
Here are the typical actions that attackers undertake when they attempt to break into your VoIP system, and the obstacles you can put in place:
Look for exposed SBCs on the internet: For ‘cold’ attacks, attackers are constantly querying the internet to look for exposed devices. One of the simplest things you can do is to stay under the radar – just avoid responding to Nmap and similar network scans.
Probe for valid extension ranges and supported endpoint types: Before they can start querying the network, attackers gather information such as extension ranges and supported endpoint types. For this, they will attempt to register on common extension ranges. If attackers have gathered more information through techniques like social engineering, they will attempt to lock one extension for a brute force attack.
What can you do? Keep an eye on multiple registration failures on a valid extension range.
Attempt to log in: Naturally, when an attacker has figured out an extension (and maybe even a password), they will attempt to log in. You can thwart many attempts by
- Tracking multiple failed attempts at logins – This would be a sign that someone is attempting to break in. The solution is to immediately block the IP address being used to attempt the logins.
- Detecting leaked or compromised certificates – This of course would require access to a list of leaked or compromised certificates
Assuming that you have access to such a list and are able to, in real-time, feed it to your SBC, you can configure the SBC to block clients that present such certificates. - Looking for rapid user sign-in attempts from globally distributed locations, also called ‘Impossible time travel’. For example, if the attacker has stolen your username and password, and logs in from Florida just a few minutes after you logged out from California – that’s a red flag.
- Identifying improbable geo-locations – For example, you’ve been logging in from California all your life, and now your username and password are being used to log in from Moscow.
If the attackers successfully break into your VoIP system, it’s still not the end of the road for you. Detection of attacker activity can take place easily inside the network because you fully control the network. You can detect, flag, and act on:
- Attempts to steal user’s personal data (user call history, speed dial, address book)
- Attempts to spy on call activity (Illegal user monitoring, wiretapping)
- Attackers covertly listen in on live conversations (Eavesdropping)
- The activity of known cyber criminals on your SBC
- Outgoing calls made by intruders (for harassment, extortion calls, etc.)
VoIP remote worker attacks are a gateway attack – opening the door to bigger and more dangerous risks, so it’s best to be smart and prevent remote worker systems from being compromised. All communication infrastructure OEMs have capabilities built into their SBCs that can reduce the risk of remote workers – reach out to your SI or OEM to discuss how you can secure your VoIP system.
Have more questions? Send me an email at securityeducation@assertion.cloud