Ransomware is pretty much the hottest topic in IT security nowadays – because of the outsize impact that a successful ransomware attack can have on a user or an organization. The first and most visible effect of ransomware on an organization is a significant disruption of operations. Later effects include loss of productivity, financial losses, and temporary or permanent loss of information.
The final, most expensive, and most long-lasting impact of ransomware is loss of reputation – would you trust any organization that could not secure its own data? Would you trust them with your data?
In today’s article, we talk about ransomware as it applies to a communications setup – how communications systems are either pathways or victims of ransomware systems.
What is ransomware?
While we all know what ransomware is, it’s best to get on the same page. Ransomware is an attack on computer systems that lock out access to them and demands payment to allow access again. Ransomware may
- lock access to the systems, so the victim may be unable to access the system at all.
- encrypt the files in the system, so you have access to the files per se, but cannot do anything with them.
- just steal the files, so they have a copy of the victim’s information.
The attackers then contact the victims and demand payment, typically in bitcoin or some other cryptocurrency. The threat is either permanent locking out from the system or files or publishing the files exfiltrated from the victim, exposing the victim to reputation loss.
On payment of the ransom, the attackers:
- provide the passphrase that can unlock access to the systems or the encrypted files
- promise to delete the files stolen from you
The encryption approach is by far the most common model of ransomware – 73% of all ransomware attacks encrypt the victim’s data and offer a decryption key. Gotta hand it to the attackers for living up to their word – 95% of all those who paid the ransom got their data decrypted. (Source: Sophos)
While there are multiple techniques used in ransomware attacks, we will look at two of them – the standard vishing-phishing and the Bazarcall attack.
Standard Phishing-Vishing Attack
Some weeks ago, I talked about vishing and how it was now a billion-dollar business. I also talked about how vishing happens in an enterprise context and here is a quick overview: Someone calls you up on your company phone and the number looks like it’s from your company itself. The reason is quite simply that the attackers have figured out, through tons of groundwork, what your company numbers look like and have spoofed their numbers to look like them. You trust this call because, well, we all trust our co-workers and a call from the company network means a co-worker is calling, right?
The co-worker informs you that some software on your systems needs to be upgraded so you need to click a link that’s been shared via email. You do a sanity check on that email origin and it, sure enough, seems to come from support-upgrade.something-like-your-company.com. Click the link, the co-worker thanks you, disconnect, and next thing you know, all your files have been encrypted. Someone else calls you and you realize you have been attacked and you now need to pay a ransom to decrypt your system.
Alternatively, the co-worker, instead of asking you to click a link, advises you to go to a website URL – support.something-like-your-company.com and log in with your username and password. When you enter the details, you’ve just opened the door for attackers to enter and encrypt your system.
The standard vishing-phishing attack is quite common now and infosec departments constantly and regularly warn people about the attack, the techniques, the approaches, and the actions to be taken. But attackers constantly learn and come up with new techniques to break into systems, and Bazarcall is one of the newer approaches.
Bazarcall
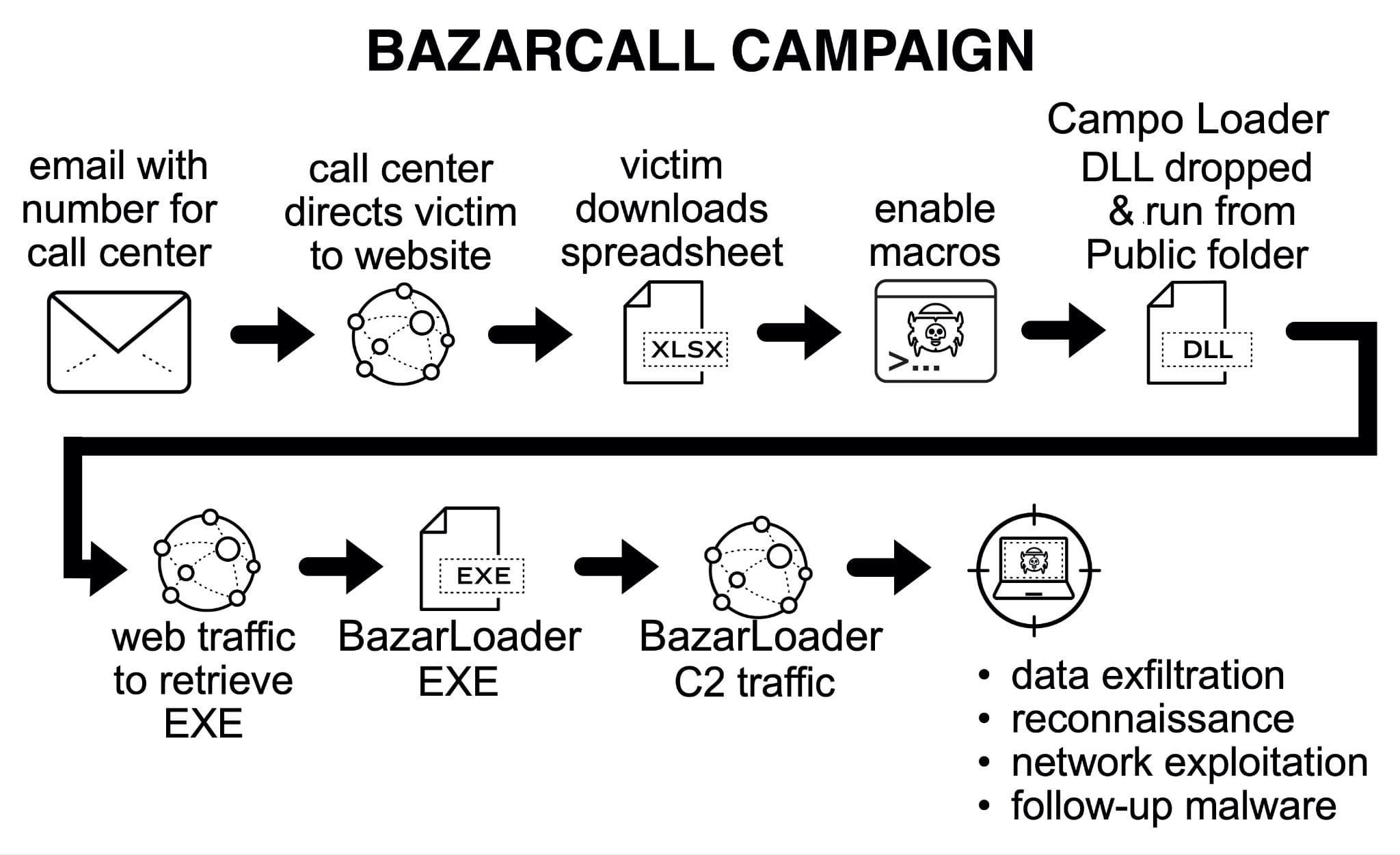
One of the shortcomings of the normal vishing-phishing attack is that it requires the victim to download an attachment and run it. A significant number of people avoid downloading any attachments. The Bazarcall ransomware attack works around this by using a guided approach.
In the Bazarcall attack, you receive an email that pressures you to call up a call center. For example, you receive an email stating that your free subscription period for ServiceX is now over and you will be billed USD 100 per month to continue with the service. The only problem is: you never subscribed to ServiceX, so you certainly don’t want to pay for a service you never signed up for. You look at the email’s origin, it’s come from servicex.cloud, so it looks legit enough. The email also has a contact number, so you call up the call center – a personable agent talks with you apologizes for the confusion, and asks you to visit a link and click the Unsubscribe button. When you do so, a file is downloaded on your computer – the agent asks you to open that file and fill in some details so that the unsubscribe takes place. Of course, the file is fake – it’s a trojan that’s downloading an application from the attacker’s servers and running the application – the outcome being the loss of access to your system or encryption of all your files. Soon enough someone contacts you with an offer to decrypt, once a suitable amount has been paid.
For a more detailed view of how Bazarcall works, see this Palo Alto Networks article.
In later articles, we will talk more about how to protect organizations against threats such as ransomware, toll fraud, and traffic pumping.
Have more questions? Send me an email at securityeducation@assertion.cloud
About Assertion:
Assertion® is a leading communication security solutions provider that empowers companies to Collaborate Confidently. Our ultimate goal is to secure every conversation through our advanced AI-enabled collaboration security solutions. We also provide holistic infrastructure security for over 38 collaboration products, including full-stack collaboration security solutions for the UC and CC stack.
