Success does not consist in never making mistakes but in never making the same one a second time — George Bernard Shaw
The same can be said of the success of your ComSec or VoIP security model.
The Cyberthreat Defense Report says that an alarming 86% of companies have been attacked more than once.
Our work with studying the security of Session Border Controllers (SBCs) paints a similar picture. In just the last month, we’ve seen ~2300 SBCs or VoIP perimeter devices targeted by reconnaissance attacks.
But more importantly, we’ve seen most SBCs being attacked more than once – by the same actors or by known malicious actors.
An SBC attack is never an isolated incident
A single incident is never just that – an isolated incident. Be it resource misutilization (toll frauds, harassment/extortion calls) or stealing call data from your agents, every attack on your VoIP system passes through the perimeter or your SBC. Every such attack gets attackers closer to breaching the VoIP infrastructure.
So, why then do companies let themselves be victims of repeated attacks?
Companies miss or ignore multiple VoIP security incidents until they escalate. They don’t often realize that they have already missed their chance to stop attackers.
Maybe it’s a false sense of security that not ‘seeing’ any attacks provides. Maybe it’s a result of the frustration that stems from false positives. Or maybe it’s just that most SBC attacks go unnoticed or unattended.
Why most SBC attacks go unnoticed
1. Inadequate monitoring and threat detection
It’s not hard to see why threat detection continues to be a gaping hole in VoIP security. Think about this.
Even for the initial stages of any attack, companies need to detect:
- Reconnaissance attempts for extension range discovery
- Unsolicited traffic
- Break-in attempts
- Unsecured calls
- Topology discovery attacks
As attacks progress, they need to be able to identify
- Brute force break-ins
- Malicious actors
- Toll fraud attempts
- Abnormal call and access patterns
- Compromised certificates
- Log tampering
- Attempts to call sanctioned countries, etc.
- Organized cyber criminals attacking the SBCs
Without actively looking out for these attempts 24×7, there’s no way for companies to detect every attack inflicted on their VoIP systems. The lack of analytics or tracking means that repeated attacks are dismissed as isolated incidents.
2) The fast-changing nature of threat intelligence
With VoIP attacks getting harder to detect and newer types being discovered each day, the threat intelligence to handle is overwhelming. Latest attack signatures, IPs of known malicious actors, the latest premium rate numbers … there’s a lot that makes it hard for companies to
- identify if they have been attacked and
- assess how serious these attacks are
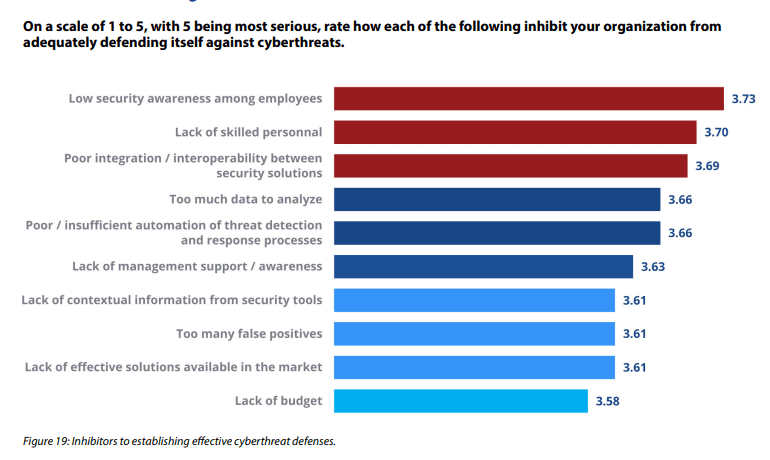
VoIP Security is a huge challenge because of the below reasons:
- Data analysis, including threat intelligence data collection, traffic, and log monitoring and analysis, is humanly impossible to do on a 24×7 basis
- Triaging is a big part of effective threat detection. Most IT teams simply don’t have the skills or the resources to do this on an ongoing basis. Additionally, false positives are a big reason for the false sense of security that leads to repeated attacks.
- Lack of effective solutions in the market purpose-built for VoIP security.
What Companies Need for Holistic VoIP Security
The role of AI in the VoIP security space is unquestionable. It’s the only way to
- Keep learning from new attacks and threats from across the world
- Improve threat, attack, and breach detection
- Monitor malicious activity
- Automate repetitive tasks without the risk of overlooked or ignored threat intelligence
Instant threat detection, 24/7 monitoring, & remediation that relies on a strong and self-learning threat intelligence is the only way ahead.
Here’s what future-ready companies can do:
- Invest in security solutions that leverage AI and ML for threat detection and monitoring.
- Focus on security analytics to ensure cybersecurity visibility extends into communication networks.
- Adopt Security Orchestration Automation and Response (SOAR) solutions that enable Voice Ops teams to work cohesively and efficiently
- Ensure policies and processes for threat monitoring, periodic configuration audits and scans, and incident response including Root Cause or Forensic Analysis and remediation.
In the cybersecurity world, there’s consensus on what a good security solution needs to accomplish.
Whatever your VoIP security model, here’s what an effective solution should do:
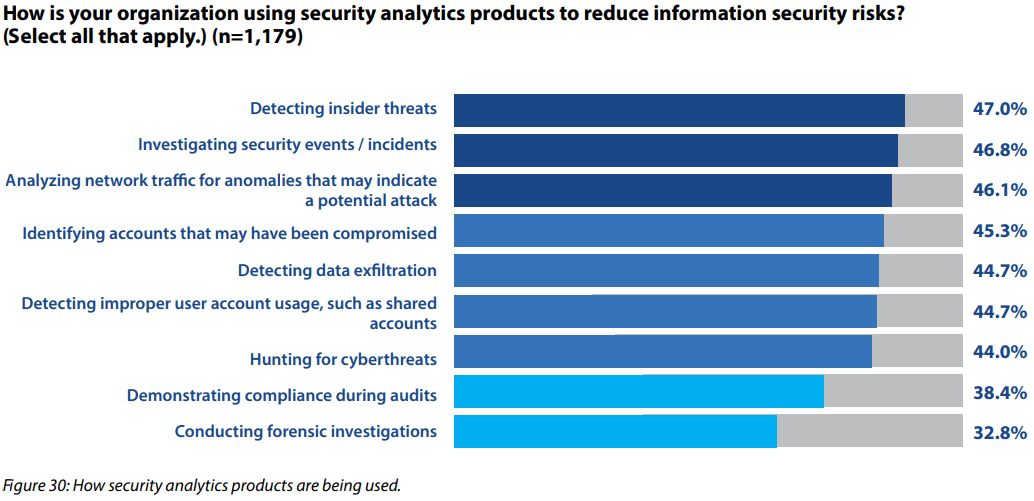
It’s easy to see the central role threat intelligence, detection, and analysis have to play in a robust VoIP security strategy. But these are ineffective without 24×7 monitoring and timely incident response systems. And that relies greatly on the skills and the bandwidth of your Voice Ops teams.
If you have any questions on implementing better security practices that can help you with VoIP security, please get in touch with us on sales@assertion.cloud
