One of the most common ways attackers compromise SIP security is via brute force attacks. Packet and registration storms are a part of brute force attacks, the objective of which is to make network components busy so that legitimate users cannot use their services. Packet storms are the most common form of brute force attacks because the tools to launch such attacks are just a download away from the Internet.
Brute force attacks using packet and registration storms on SIP servers are increasing exponentially. Experts at CERT.br noticed the increasing attacks on SIP servers and decided to launch an investigation. They gathered data by emulating SIP servers in the Brazilian Internet space using 50 low-interaction honeypots, based on Honeyd, and collected data about these attacks for 358 days. They determined that attackers mainly target port 5060 of the SIP network in the following sequence:
1. Scanning for SIP servers.
2. Enumerating identified SIP servers. The attackers try to enumerate the server configuration, available extensions, etc.
3. Using brute force attacks to try to access extensions that are protected with weak passwords.
4. Abusing the network resources. After gaining access to PBX extensions, the attackers try to call external PSTN numbers, usually to place international calls.
How attacks happen
Criminals attack SIP enterprise networks using different types of SIP requests or call control messages, mainly SIP registration requests, to flood the SIP proxy server and consume all of its resources. They might also use an army of botnets to send SIP requests to the SIP registrar server, which maintains records of user agents. These SIP registration requests, which might be in the millions, overwhelm the SIP server and prevent the server from servicing legitimate registration requests, thereby causing a service outage.
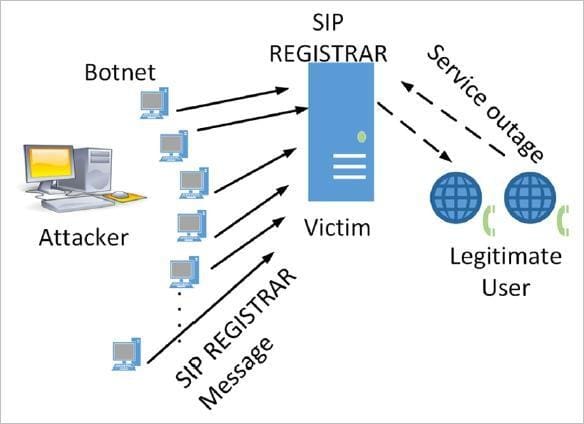
SIP registration storms cause SIP servers to attempt to service all SIP registration requests, which causes SIP clients to unregister and attempt to register again. Among the SIP registration storms, the registration requests of legitimate SIP clients are lost, and the SIP server becomes unresponsive causing a network failure. This problem is exacerbated because the SIP clients keep trying to register with the server again even after the SIP server failure, unaware that the server is unreachable. Even after the server starts working again, it is again overwhelmed by the SIP clients trying to register with it and complete the handshake. Registered SIP clients cause further problems to the now-working server by sending additional requests to gain access to other services.
Signs of a SIP flood attack include SIP clients disconnecting and registering multiple times, slow network connections, and continuous heavy use of bandwidth.
The primary method of preventing packet and registration storms is to identify good registration messages. You can create rules in your firewall for this, but registration storms might still flood the SIP trunk and consume the bandwidth even before reaching the firewall. This is why Session Border Controllers deployed at the edge of your network are crucial for detecting such SIP registration storms and blocking the traffic flood.
How SBCs defend against such attacks
SBCs prevent attacks mainly through the configuration of Access Control Lists, DoS and DDoS protection, appropriately sized traffic queues, and trust level settings that blacklist endpoints that become abusive. Additionally, SBCs also use rate limiting to enforce limits on parallel calls, call rates, and bandwidth usage. SBCs can enforce these limits globally in the network or limit traffic using keys such as source IP addresses or SIP From addresses.
The primary defense that SBCs use against SIP registration storms is a dynamic blacklist in Access Control Lists. SBCs temporarily prevent SIP clients that try to register beyond the configured threshold by adding the SIP clients in this blacklist. If, or rather when, criminals try to launch a brute force attack using SIP registration storms, SBCs blacklist the registration requests and prevent the attack flood.
Moreover, timeouts configured in SBCs for registration and authentication procedures when SBCs receive requests with invalid credentials slow down potential brute force attacks by preventing further registration requests.
If your SBC is not configured for Access Control Lists and Dynamic Blacklists, this configuration should have your immediate attention. Assertion® SecureVoice™ can identify issues in your configuration and help you with remediation tips to harden your VoIP systems against brute-force attacks.
Take the first step to SIP security
With criminals increasingly launching brute force attacks on SIP servers using SIP floods, such as SIP packet and registration storms, SBCs’ enforcement of configured policies and limits on the inflow of traffic from the public Internet in SIP networks plays a crucial role in preventing attacks and protecting enterprise networks from criminals. You can improve the protection that SBCs offer by having policies and configurations tailored specifically to your network topology and scanning every call into and out of your VoIP network.
We can help you.
