In a systematic approach to preventing attacks on your communication systems, the first thing to do is to protect the network plane.
Most organizations nowadays use the same IP-based network for data and voice. This means that a break-in into the data systems automatically impacts the voice network as well. Voice systems, which were more difficult to break into, are now exposed to the same challenges as data systems. This expanded attack surface must therefore be secured against the threats of eavesdropping, user impersonation, toll fraud, and DoS.
Securing the network to prevent attacks on the voice systems is not just a border-level problem – it requires a defense-in-depth approach. Without that, your entire voice infrastructure is susceptible to the same attacks that can be inflicted on data networks, with the same tools as well. This article provides some suggestions on how you can protect your voice systems on the network plane.
Prevent physical access
This is a simple but sometimes overlooked point – as VOIP networks are now indistinguishable from data networks, physical access to the infrastructure must be dealt with the same level of paranoia. Some guidelines on physical access:
- Video-record all movement in server rooms that host communication equipment.
- Keep server cabinets locked, with access to keys logged and controlled.
- Log and control all access to server rooms.
Preventing access to voice packets
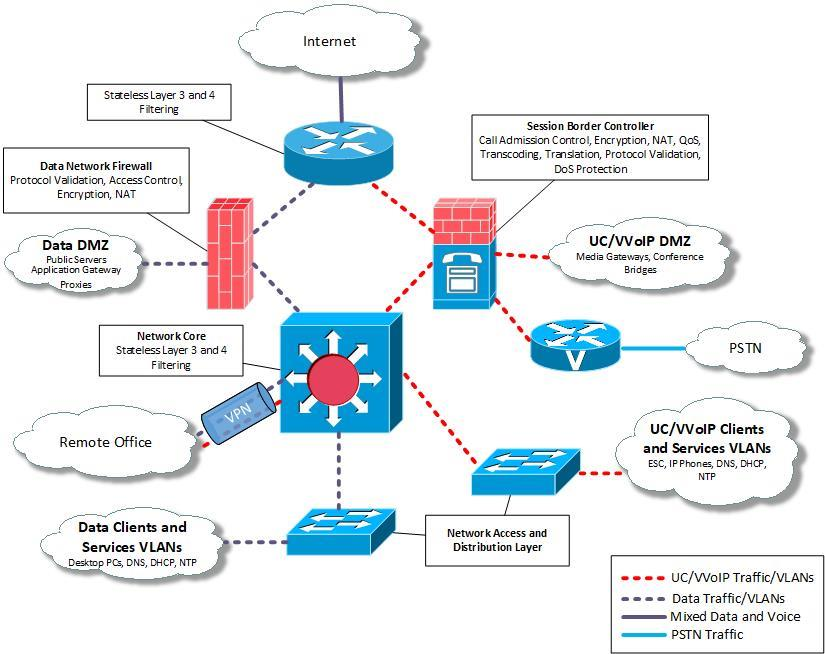
Even if you are using a common IP network, separate the data network from the voice network by using logical separation techniques like Virtual LANs (VLANs). Using VLANs to separate data from voice makes sure that weaknesses in one network do not impact another – a key principle of defense-in-depth.
Naturally speaking, the logical separation must be taken to its, well, logical end – the border must be maintained, and gates should be guarded:
- Identify specific points in the network where interchange between voice and data traffic can take place – at these points, implement application-layer firewalls to monitor, control, and examine all traffic traversing from one network segment to the other.
- Keep only network devices that are used for voice traffic in the voice VLAN.
- Duplicate ‘Essential’ network services, such as NTP, DNS, DHCP, and so on – one set for the data VLANs and one for voice.
- Control traffic access to the voice VLAN by using stateful packet filtering devices. Use multiple parameters to filter – IP address, port, and protocol.
- On stateful packet filters, configure access control lists that allow voice/video endpoints to connect only to the V/VOIP servers.
- If any devices must necessarily be shared between data and voice VLANs, place them in the DMZ and control access through proxies.
Preventing eavesdropping
One of the biggest security risks that voice networks face is eavesdropping – attackers who break into the network may listen in to sensitive conversations. To prevent eavesdropping, do the following:
- Encrypt all voice and video traffic from end to end – in motion and at rest. This can become significantly more complex if you run a global organization. From a technology perspective, two key challenges stand out here – ensuring that the latest encryption standards are available and used across every device on the communication pathway, and ensuring that carriers of SIP traffic across multiple geographies support your encryption standards and requirements.
- Enable port security for all switches, so that any device that attempts to connect to the network must authenticate itself first.
Preventing network availability issues
Network availability issues can occur for two reasons: environmental issues and malicious actors.
Environmental issues are a well-known concern and have been around pretty much forever. These include power outages, system failures, and so on.
Malicious actors have also been around for a long time, but the nature of the threats has been changing. VVoIP networks now must deal with Denial of Service at multiple levels – a well-known threat in the data world. DoS attacks can be triggered by attackers who
- identify and leverage software vulnerabilities in VVoIP devices to either disable them or to overload them
- overload the network by sending more packets than it can handle
The first situation can be handled by patching regularly and keeping the software up-to-date.
The second situation requires more work:
- Rate-limit the traffic to VVoIP systems by using devices such as SBCs.
- Enable QoS on all devices so voice/video traffic gets higher priority.
- Identify calls coming in from well-known attacker-owned numbers and block them.
- Identify packets coming in from known or suspected IP addresses and block them.
Preventing protocol issues
Communication services, like data services, depending on a host of support services that form the foundational structures of an IP setup. These include DNS, DHCP, and NTP servers. Preventing failures of these services is therefore critical to maintain functioning VVoIP services.
DNS
The Domain Name Service is critical for the proper functioning of literally every device on any IP network, including voice and video systems. To protect them, protecting DNS is necessary.
- Use dedicated DNS servers for the voice VLAN, separate from DNS servers for the data VLAN.
- Implement DNSSEC – security extensions that bring in authentication and integrity to DNS. With DNSSEC, your DNS server can be sure that the data received from another DNS server is correct, uncorrupted, and from the right provider.
- Implement forward-confirmed-reverse DNS, which ensures that the forward (name-to-address) and reverse (address-to-name) DNS entries for an IP address match each other, a different authentication method.
- Prohibit zone transfers, which allow malicious actors to gain information about servers in the network.
NTP
Voice and video protocols are time-sensitive – so NTP servers are necessary and must be protected.
- Use dedicated NTP servers for the voice VLAN, separate from NTP servers for the data VLAN.
- Make sure that the NTP servers being used are up-to-date and use newer versions of NTP, which support authentication and integrity.
DHCP
Since voice and video endpoints form a large cohort and IP addresses are in limited supply, DHCP becomes critical for IP address management.
- Enable DHCP snooping, which helps identify and prevent rogue DHCP servers from taking control of endpoints.
- Enable port security for all switches, so that any device that attempts to connect to the network must authenticate itself first. This prevents rogue DHCP clients from being able to get IP addresses from the pool.
This is just a starting point – a significant amount of additional work needs to be done to secure the network plane of your communication systems, but this is a good start. Successful implementation of these guidelines prevents a lot of attacks and makes breaches much more difficult. That said, these guidelines are mostly preventive in nature – the attempt being to prevent successful attacks. Networks are attacked, it’s true, but it’s also true that all networks are eventually breached. And that’s what’s missing in this article – how to identify breaches early so that you can react quickly. We shall discuss that in a later series.
This article uses the NSA VVoIP Security document as a guideline.
Have more questions? Send me an email at securityeducation@assertion.cloud
About Assertion:
Assertion® is a leading communication security solutions provider that empowers companies to Collaborate Confidently. Our ultimate goal is to secure every conversation through our advanced AI-enabled collaboration security solutions. We also provide holistic infrastructure security for over 38 collaboration products, including full-stack collaboration security solutions for the UC and CC stack.
