When customers call an enterprise, how does the organization ensure that the customers are who they claim they are? The well-intentioned response of most companies is to authenticate customers by getting them to answer a few verification questions – typically using an IVR to save agent time.
This article explores the vulnerabilities of such IVR knowledge-based authentication and presents a solution to safeguard customer accounts from IVR scams.
IVR Fraud: Why Knowledge-Based IVR Authentication can be a Vulnerability
IVR systems, designed to streamline customer interactions, often rely on knowledge-based questions for customer identity or account verification. This knowledge-based authentication (KBA) approach relies on asking callers questions that only the account holder should know. This may include security questions such as the name of the street they grew up on or the name of their elementary school.
But these questions, and as a result, this approach, are no match for today’s fraudsters.
They use elaborate data harvesting to collate potential answers pertaining to targeted high-value customers, or try repeatedly till they make their way in.
And answering these questions is only a matter of time and persistence for them.
The time and effort are almost always worth it – to uncover recent transactions, past behavior, and access other details that can help them conduct fraud through other channels more successfully.
In addition, knowledge-based authentication (KBA) has another key drawback: If you increase the number of questions for increased security, it impacts the customer experience — with customers having to spend more time on the call answering tedious security questions before achieving their goal.
The Security Gap in IVR Knowledge-Based Authentication
Traditional IVR systems lack the ability to identify fraudulent account access attempts in real-time. They rely solely on pre-set knowledge-based questions and may not have the capability to detect suspicious patterns or anomalies during the interaction.
This is why Gartner advises organizations to “deploy a layered defence of identity proofing, fraud detection and authentication capabilities, closely coupled with tighter integration into cross-channel fraud detection systems.”
The Solution Approach: Leveraging Call Behavior Analysis
A comprehensive solution is required to prevent fraud and authenticate customers effectively. By utilizing machine learning and network signaling data, call behavior analysis can identify anomalous call behavior patterns and potential fraudsters.
However, you need a range of behavioural analysis that can help identify potential fraudsters. This could include anything from analysing the caller’s location to seeing the calls they’ve made in the past to where they are located. Analyzing these factors in real time allows enterprises to build a caller’s risk profile before connecting them with the IVR or contact center agent.
Enterprises also need to analyze the calls to your IVR for repeated disconnects, rejections, and short duration calls to detect attempts to crack the KBA questions.
This enables them to block or flag suspicious calls, effectively intercepting fraudsters before they gain access to sensitive information.
Preventing IVR Account Takeover Scams with Assertion® SecureVoice™
Assertion® SecureVoice™ is designed to be a powerful VoIP security solution that combats IVR account access scams among several other VoIP scams. By leveraging advanced analytics and real-time call analysis, It identifies suspicious patterns and behaviors, ensuring the security of customer accounts. Here’s how Assertion® SecureVoice™ tackles this challenge:
- Intelligent Call Analysis: It employs AI-powered algorithms to analyze each incoming call, detecting subtle cues and patterns that indicate potential fraudulent account access attempts. By continuously monitoring calls in real-time, Assertion® SecureVoice™ can identify unusual behavior and flag suspicious interactions for immediate investigation.
- It analyzes the calls to your IVR and detects short duration calls, repeated disconnects, and other behaviors indicative of IVR break-in attempts.
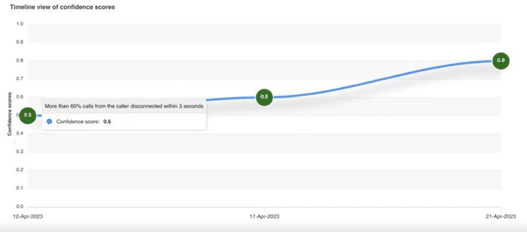
Confidence scores that are updated in real time to continuously track the behavior of suspicious callers
- Behavior-based Anomaly Detection: Assertion® SecureVoice™ studies your enterprise’s calling patterns and your callers’ behaviors. Any deviations from these established patterns trigger alerts, enabling you to take proactive measures and prevent unauthorized access attempts.
Over to You
IVR account takeover scams pose significant risks to both you and your customers. If undetected, these scams can result in financial losses, reputational damage, and the compromise of customer trust. Moreover, as scammers continue to refine their tactics, the likelihood of successful account takeovers is only going to increase.
Preventing such scams requires a proactive and intelligent solution that can detect and prevent unauthorized access attempts in real-time. Assertion® SecureVoice™ is a formidable defense against IVR account takeover scams. By leveraging advanced real-time call analysis, behavior-based anomaly detection and 24×7 call screening. Stay one step ahead of scammers and fortify your IVR system with Assertion® SecureVoice™.
Sign up for a zero-cost POC by emailing us on sales@assertion.cloud
