The GSMA Whitepaper, issued in Feb 2020, provides a good roundup of the various solutions and mitigations being considered for the problem of illicit robocalls. In addition, the ATIS Paper, issued in Feb 2021, also provides an overview of the illicit robocalling problem along with some mitigation techniques and their challenges. The key approaches, according to them, are as follows:
Blocklisting Robocalls
The simplest technique to prevent spam or scam robocalls is the Blocklist. Blocklists can be super-simple – the user simply adds spam/scam numbers immediately after they are received, and if the blocklist is integrated into the phone, new incoming calls can be checked and blocked.
Crowdsourcing Blocklists
Crowdsourcing Blocklists are already very popular with consumers – Truecaller, Robokiller, and YouMail are some examples, though all of them now supplement crowdsourcing with other techniques to identify illicit robocalls.
At its simplest, a crowdsourcing blocklist approach consists of a database and an app. Users install the app and mark every incoming call as spam or not spam. Spam numbers are then kept on the common database, which is looked up for all incoming calls by the app.
The big challenge with blocklists (crowdsourced or otherwise) is caller-ID spoofing – illicit robocallers regularly spoof their caller IDs, making it difficult to identify where the incoming call is originating from. Other challenges also exist –
- Legitimate callers get blacklisted – making it difficult for honest, legitimate businesses to transact business as usual. For example, I often get calls from a food delivery person, and they’re marked as spam.
- Emergency notification numbers etc. might get blocked.
Most of the crowdsourcing blocklist providers enable APIs that enterprises can use to get the same value that consumers get.
STIR/SHAKEN
Two caller-ID authentication technologies being aggressively promoted and deployed across the US are Secure Telephony Identity Revisited (STIR) and Secure Handling of Asserted information using toKENs (SHAKEN). Pushed by the FTC, service providers across the US are rolling out these standards across their entire network. We will discuss STIR/SHAKEN in more detail later in this series, but here’s an overview:
The STIR standard is based on three key IETF RFCs – 7340, 8224, and 8226. These documents together describe a model of using and verifying the credentials of parties that control phone numbers. A calling party asserts that it is authorized to use the phone number associated with the caller ID and parties along the chain must use authentication services to verify that the assertion indeed is correct and true.
Complementing the STIR standard is SHAKEN. The SHAKEN [ATIS-1000074] specification creates a framework that pulls together the STIR protocols – if you are making phone calls using SIP, SHAKEN validates that you are authorized to do so with the phone number you are using.
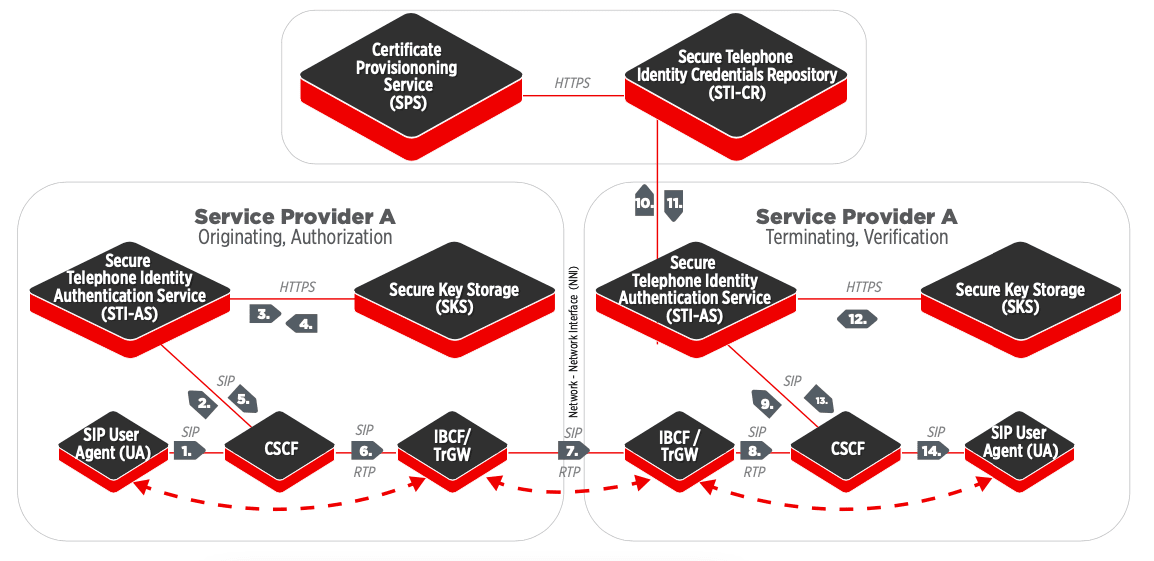
With SHAKEN, recipients can have an adequate level of confidence in the originating identity, including originating communications – regardless of whether VOIP or TDM/SS7 is used by the caller.
Even when the STIR/SHAKEN framework is fully deployed, international and wholesale traffic will still be an issue for spam/scam robocalling. Also, illegal Caller ID spoofing cannot be detected from this kind of traffic. Providers may mark this kind of traffic as unverified, but that’s an excessively broad brush to paint all international/wholesale callers with.
One more thing to note is that STIR/SHAKEN is not designed to block robocalls – it is designed to authenticate the ID of the calling party. What happens when a call is authenticated (or not!) is a decision left to the service provider.
STIR Out-of-Band Architecture
STIR works best in a pure SIP environment – everything from the call origination to call termination must be SIP. However, the reality today is a mixed environment – most calls
traverse the legacy Public Switched Telephone Network (PSTN) at some point, which means STIR data is often lost/dropped. Also, today, one or both endpoints is often PSTN endpoint.
STIR Out-of-Band architecture proposes that the token objects that convey information about the participants involved in communications can be sent directly to the terminating devices/networks over other networks, such as the Internet.
Analytics and Authentication Services
STIR/SHAKEN is a big step forward, but for both enterprises and individuals – it may not be enough. As mentioned earlier, STIR/SHAKEN leaves it up to the service provider to act on the authentication information of the originating party – and many service providers may simply choose to label the call and pass it on to the terminating party anyway. It also does not address the issue of wholesalers or international calls, which are very common routes for robocalls, meaning that a significant number of robocalls will still get through. If you are an enterprise, this means that your employees will still receive the calls, admittedly with better labeling (“Potential Spam!”).
To address this concern, you can work with analytics and authentication services that are dedicated to assessing how legitimate calls are and assigning confidence scores to them. Using information such as the location of the originating call compared to the destination, the number of such calls during a certain period, typical caller behavior (“spikes and crashes”) and so on – these services can provide enterprises with a better assessment of incoming call quality and suggest actions (“allow/label/block”). This can be fully automated – SBCs can forward the call to the service, which can return the call back to the SBC with an assessment.
There are other ideas and techniques that address the problem of illicit robocalls, with varying levels of effectiveness, but the truth is: that the economics of bulk robocalling are so solid that we cannot really expect this pandemic to end. For now, these measures will provide us and our customers some relief from the incessant robocalls, but eventually, the robocallers will figure out how to avoid or bypass the protections provided by STIR/SHAKEN, and we will have to learn how to protect ourselves again…
Have more questions? Send me an email at securityeducation@assertion.cloud
About Assertion:
Assertion® is a leading communication security solutions provider that empowers companies to Collaborate Confidently. Our ultimate goal is to secure every conversation through our advanced AI-enabled collaboration security solutions. We also provide holistic infrastructure security for over 38 collaboration products, including full-stack collaboration security solutions for the UC and CC stack.
