If you are responsible for securing your organization’s IT infrastructure, you need to know some things about your communication networks, and how to secure them, because they now have a direct impact on your data security. And you need to bring your communication network into the IT security fold.
A little background: The days of PRI connectivity to your telecom operator are over. SIP is the way forward and has been adopted by all major telecom operators worldwide. If you need PSTN connectivity to your office or call center today, chances are you will end up buying a SIP trunk.
But SIP is prone to similar kinds of attacks that HTTP, for example, faces today. In short, attackers have their targets set on your communication systems.
Attacks on communication networks have been skyrocketing, especially as the attack surface of communication networks has multiplied, thanks to the explosive increase in remote working. And lateral attacks – hackers breaking through the communication network to leap into the rest of the data infrastructure – that once used to take two hours now take 20 minutes
In short, time for a quick primer on how to secure your communication perimeter.
Say Hello to Session Border Controllers
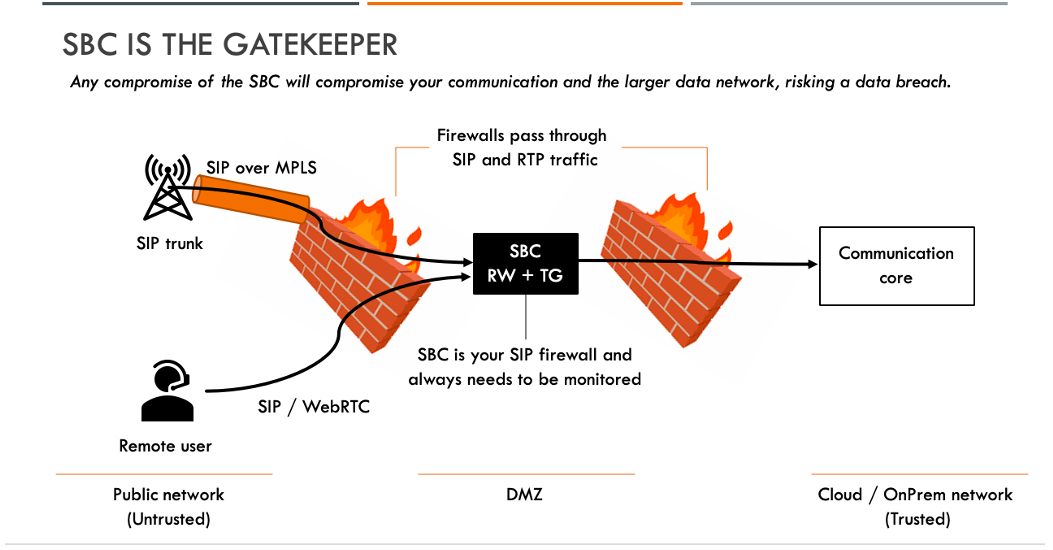
A Session Border Controller (SBC) is an integral part of Voice / Video communications today. Whether you are using Zoom or Teams meetings, cloud communication providers or traditional IP telephony PBX, you need an SBC to connect to your telecom operator (AT&T, T-mobile, Verizon, etc). SBC has one leg towards the telecom operator and another leg towards your enterprise communication system (Trunk Gateway mode, TG), acting as a protection system for your communication system.
Just as firewalls protect your data perimeter, SBCs do the same for your communication perimeter. An SBC is a gateway device that sits on your enterprise fence and acts as a proxy device – accepting and managing both Trunk and User connections for you. In simple words, SBC is a voice/video firewall. Being a device that sits on the internet and in your DMZ, it needs as much security attention as your firewalls and web proxies.
An SBC is a gateway device that sits on your enterprise fence and acts as a proxy device – accepting and managing both Trunk and User connections for you. In simple words, SBC is a voice/video firewall. Being a device that sits on the internet and in your DMZ, it needs as much security attention as your firewalls and web proxies.
Your SBC also has another purpose – it enables remote workers to get communication services without having to sign in to their VPN. Routing real-time communication traffic like voice and video over VPN, adds delays and kills the experience. Everyone needs always-on connections and an SBC gives you just that – enabling your remote workers to be signed into their enterprise phones at all times. In that mode, an SBC has one leg on the internet to allow remote users to connect to it, and another leg towards your enterprise communication system.
Most companies typically separate their Trunk gateway SBCs from Remote worker SBCs. Though a single SBC can perform both roles, keeping them separate is done for management convenience, enhanced security, and improved performance.
Infosec the world over has paid a lot of attention to securing the endpoint, the data perimeter cloud access, but has neglected collaboration security. With remote working becoming a more permanent feature, and with more telecom operators pushing enterprises to move to SIP trunks, an SBC is a reality for most of us. And with it, comes new risks and an expanded threat surface that you have to manage.
Securing your SBCs for Effective Communication Security
Guarding the perimeter is sensitive business – one mistake and you’re looking at a breach.
SBCs are security devices, and therefore have inbuilt features to ensure a default level of security. But, like most firewalls, SBCs have a lot of configurations, and one bad certificate, TLS cipher or bad permissions in place can make or break your fence. Do you want to take a chance? Or invest in a periodic assessment of SBC’s health?
Knowing the true status of your SBC’s security can help you
- prevent data leaks through Man-in-the-middle and eavesdropping attacks by ensuring robust encryption and security standards
- prevent potential threats by discovering holes in your SBC’s security configuration that weaken your security posture.
- Detect attacks underway and breaches that may have already occurred, through an automated analysis of your logs.
Assertion® SecureVoice™ can help secure your VoIP systems by analyzing every SIP session and screening every call. Talk to us to know more.