Over the last two weeks, we’ve spoken about securing the network and perimeter, so this week, we talk about the risks to communications endpoints and guidelines for securing them. I have mentioned in the earlier article that endpoint insecurity is not a systemic risk and I stand by that statement. However, they do impact productivity for users and may cause significant overhead for administrators who would rather focus on systemic, long-term concerns. Also, compromised endpoints may lead to loss of data, especially in call center scenarios, where agents have access to customer information. This kind of information leakage, while minor, may also lead to embarrassment and reputational damage for the company.
Endpoints have been evolving over the last few years – from pure hardware devices with limited functionality to pure software apps with far more capability to work autonomously from the PBX – look at Teams or softphones from Avaya and Cisco, for example. But the increase in capability and complexity has brought with it additional risk – the attack surface for endpoints has increased. Even headphones today are really smartphones – they allow apps to be installed, and they run full operating systems (often Android), so the security risks have multiplied.
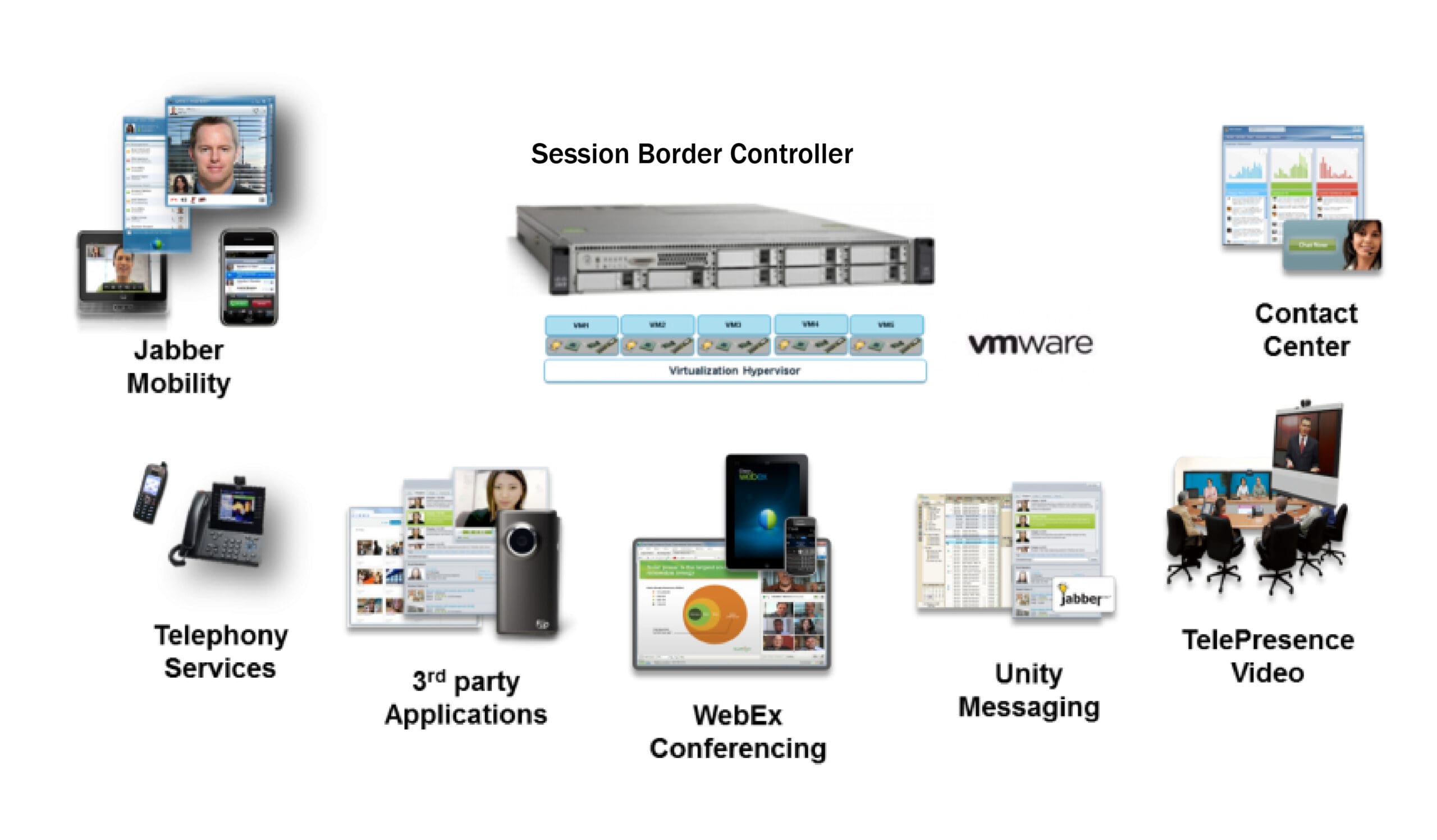
Risks to Endpoints
Risks from software vulnerabilities
If you are running an endpoint that uses Android, it’s obvious that every Android vulnerability would be a matter of concern for you. And if you are using a softphone, then every vulnerability on that OS is an issue. And if you are using the softphone through the web browser, then every web browser issue is a problem. In short, software vulnerabilities in the environment of the endpoint are a risk to the endpoint itself.
An attacker can compromise the environment to gain control of the endpoint and surreptitiously gather information by enabling audio or video capabilities, tampering with remote management capabilities, or at the least, denying service to the endpoint.
Risks from third-party apps
If you are running a hard phone with smart capabilities, you possibly have the capability to download and install third-party apps on your hard phone. Similar capabilities also exist in softphones – the ability to install apps, applets, plug-ins, and so on. While these apps can potentially bring in new capabilities, they also provide new pathways for attackers to gain control of the endpoints. As in the case of software vulnerabilities, information leakage, service disruption, and service denial at the endpoint are the biggest issues.
Another risk you face from third-party apps is that they may be malicious – instead of a third-party app’s vulnerabilities being exploited, we are talking about the app itself masquerading as useful but in fact being malicious. Several third-party apps, even from well-known providers, offer useful services, but secretly and without transparently informing the user, they steal data from the system. The more extreme versions may serve as launchpads for other attacks that aim at other call processing systems.
Remote management risks
Endpoints are usually designed from the ground up for remote management. Hard phones may download firmware and configuration files from systems, softphones may download configuration information. If your organization is a large one, there is a solid chance that your administrators need to support a wide variety of endpoints, often from a multitude of vendors. Also, for every vendor, multiple versions of endpoints are probably being supported. Every version presents potentially different risks and managing each version is an overhead.
Remote management may be carried out in any number of ways, ranging from DHCP to SNMP to a simple download of firmware from call servers. To secure your endpoints, you need to examine and address each of these methods.
Network connectivity risks
How do your endpoints connect to the network? The original model of a separate physical network for communication systems is almost completely phased out. In the case of Ethernet, hard phones often have ports that your laptops/desktops can connect to, so the hard phone provides a bridge – getting access to the traffic meant for the laptop/desktop and vice versa.
Another couple of risks
- Bluetooth integration
- Wi-Fi connectivity
In general, every connection type/connection protocol brings new risks and multiplies the attack surface area for endpoints.
Application Integration
I love that when my phone rings, I can choose to pick it up from my laptop. I also love that I can click a phone number on my laptop and my phone makes the call. Essentially, while I have been talking about maintaining a clean separation of data and voice systems, this is an example of the benefits of close integration between the two systems. But this level of integration brings new risks – it means that more applications are communicating with my endpoints and that in turn means every one of those applications is potentially a vector for new infections, attacks, and compromises. My address book is synced between my phone and my laptop and my web account – a malicious actor can delete its contents from one, and the deletion will affect all the systems – integration is useful but it is also how infections spread.
Endpoint Protection
To protect the endpoints, here are some things you can do:
- Either disable or strictly control the ability to install applications on the endpoints, regardless of whether they are hard phones or softphones. Only allow applications, applets, and plug-ins that have been tested, approved, and certified. If your endpoints lack support for such control and management capability, they are not ready for the enterprise.
- Have a solid and strong patch management system in place – update all endpoints with the latest security patches, after appropriate testing is done, of course.
- Where possible, disable direct internet access to endpoints – connections must be mediated through the communication system, and in the case of remote systems, make sure the endpoints connect to the communication system via VPN.
- Ensure that configuration files and firmware are cryptographically signed, and ensure that the verification key is loaded on the endpoints in a secure manner, while the signing key is kept in a safe and secure place away.
- If you use SNMP to manage endpoints, make sure it’s SNMPv3 over TLS/DTLS.
- Disable all network connections that are not needed or cannot be admin-controlled. If Bluetooth/Wi-Fi connectivity is not required, disable it.
- When softphones are being used, separation of data from voice traffic is infeasible, so separate laptops/desktops that need these softphones and filter all traffic – move all voice and video traffic to a separate VLAN where the rest of the communication infrastructure is kept.
All of these measures take inspiration from the NSA’s excellent guidelines on VVoIP security.
Have more questions? Send me an email at securityeducation@assertion.cloud
About Assertion:
Assertion® is a leading communication security solutions provider that empowers companies to Collaborate Confidently. Our ultimate goal is to secure every conversation through our advanced AI-enabled collaboration security solutions. We also provide holistic infrastructure security for over 38 collaboration products, including full-stack collaboration security solutions for the UC and CC stack.